AWS Control Tower makes it easy to set up and manage a secure multi-account AWS environment. AWS Control Tower uses AWS Organizations to create so-called landing zones for ongoing account management and governance based on our experience working with thousands of customers.
If you use AWS CloudFormation to manage your infrastructure as code, you can use AWS Control Tower Customization to customize your AWS Control Tower landing zone. This solution helps you deploy custom templates and policies to individual accounts and organizational units (OUs) within your organization.
But what if you use Terraform to manage your AWS infrastructure?
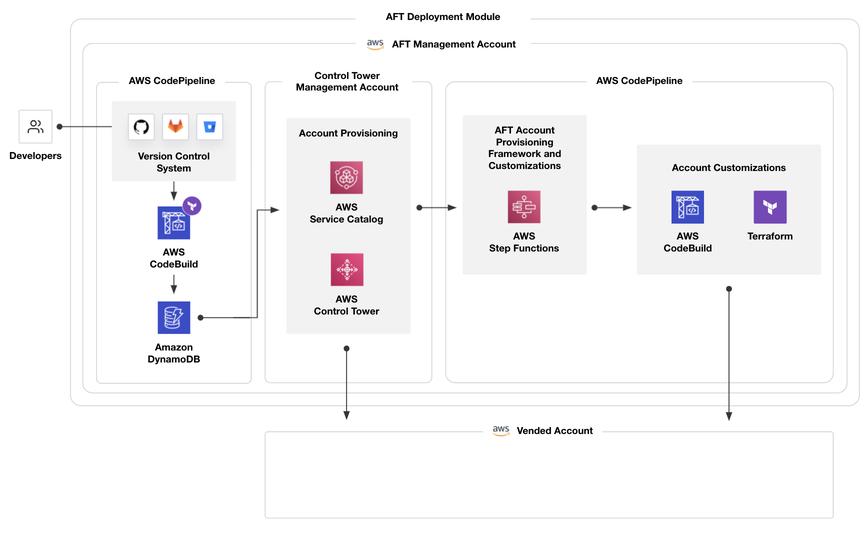
As of November 29, 2021 (US time), AWS Control Tower Account Factory for Terraform (AFT) is now available. This is a new Terraform module managed by the AWS Control Tower team that allows you to provision and customize AWS accounts in Terraform using deployment pipelines. You can store your development pipeline source code in AWS CodeCommit, GitHub, GitHub Enterprise, or BitBucket. AFT can automate the creation of a fully functional account with access to all the resources you need to be productive. This module works in conjunction with Terraform Open Source, Terraform Enterprise, and Terraform Cloud.
Now let's see how it works in practice.
Using AWS Control Tower Account Factory for Terraform First, create a main.tf file that uses the AWS Control Tower Account Factory for Terraform (AFT) module.
module "aft" {source = "git@github.com:aws-ia/terraform-aws-control_tower_account_factory.git"# Required Parametersct_management_account_id= "123412341234"log_archive_account_id= "234523452345"audit_account_id= "345634563456"aft_ management_account_id = "456745674567"ct_home_region= "us-east-1" tf_backend_secondary_region = "us-west-2"# Optional Parametersterraform_distribution = "oss"vcs_provider = "codecommit"# Optional Feature Flagsaft_feature_delete_default_vpcs_enabled = falseaft_feature_cloudtrail_data_events= falseaft_feature_enterprise_ support=false}< /pre>The first six parameters are required. As a prerequisite, you must pass her the following four AWS account identities in your AWS organization:
Next, we need to pass in two AWS Regions.
Other parameters are optional and set to default values in the
main.tffile above, as follows:Such feature flags are disabled by default and can be omitted unless you want to enable them.
First, initialize the project and download the plugins.
terraform initThen log in with your AWS Control Tower administrative account using to start the deployment.
terraform applyConfirm with
Yesand the deployment will complete after a while.
Now use AWS SSO again to log in with your AFT admin account. The AWS CodeCommit console has four repositories that you can use to customize your account created with AFT.
These repositories are used to automate account creation in pipelines managed by AWS CodePipeline.
Currently, all four of these repositories are empty. First, use the code found in the
sources/aft-customizations-reposfolder in her GitHub repository for the AFT Terraform module.Using the example from the
aft-account-requestrepository, we have a template for creating some AWS accounts. One of the two accounts is for software developers.Create specific account customizations to quickly increase software developer productivity. The template sets the parameter
account_customizations_nameto the same value asdeveloper-customization.Next, create a
developer-customizationfolder in theaft-account-customizationsrepository. Place a Terraform template in this folder to automatically create an AWS Cloud9 EC2-based development environment for new accounts of that type. Optionally, you can extend this with Python code to call internal or external APIs, for example. Using this approach, every new software developer account has a development environment ready as it moves through the delivery pipeline.Push your changes to the
mainbranch (first to theaft-account-customizationsrepository, then toaft-account-request) . This will trigger the pipeline execution. After a few minutes, your two new accounts will be ready to use.Accounts created by AFT can be customized based on your specific requirements. For example, each account can have its own security settings (such as IAM roles and security groups) and storage (such as preconfigured Amazon Simple Storage Service (Amazon S3) buckets).
Region availability and pricing AWS Control Tower Account Factory for Terraform (AFT) operates in all regions where AWS Control Tower is available. There are no additional costs for using AFT. You pay for the services you use in your solution. For example, when you set up AWS Control Tower, you start incurring costs for AWS services configured to set up your landing zone and mandatory guardrails.
In building this solution, we worked with HashiCorp. His Armon Dadgar, co-founder and CTO of HashiCorp, said: “Managing a cloud environment with hundreds or thousands of users can be a complex and time-consuming process. easily achieve consistent governance and compliance requirements.”
This pipeline provides the account creation process. This allows you to monitor when account provisioning is complete and trigger additional Terraform modules to further customize and extend your account. You can configure your pipeline to use your own custom Terraform modules, or choose from publicly available Terraform modules for common products and configurations.
Simplify and standardize AWS account creation with AWS Control Tower Account Factory for Terraform.
–Danilo
The original is here.






![Advantages of "Gravio" that can implement face / person recognition AI with no code [Archive distribution now]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_6/2022/2/25/98ceaf1a66144152b81298720929e8e7.jpeg)